About Keys
14.03.2025
A loosely structured index of the current approaches within or nearly within reach.
Summary
Below is a very compressed survey on methods for key management, access control and key encapsulation. I was unsure about the variance at the level of general approach. What I've found is that the variance is low. There are really only a few ways to make a pie here. As always with cryptography, the devil is in the details.
Use these notes as a map for further exploration.
Notes
1. Foundational Approaches
Classical Symmetric & Asymmetric Schemes
• Kerberos (symmetric keys, Key Distribution Center)
• PKI (public-key certificates, roots of trust, TLS/SSL)
• Hybrid key management (combining symmetric + asymmetric)
• Symmetric Key Encryption (e.g., AES, ChaCha20): Requires secure key exchange or pre-shared secrets. Potentially higher throughput but burdens key distribution.
• Asymmetric Key Encryption (e.g., RSA, ECC): Key length selection is crucial to maintain security (e.g., 2048-bit RSA is borderline, 3072-bit or 4096-bit recommended; similarly, ECC sizes like P-256 or Ed25519 are favored in modern systems).
• Common Pitfall: Overlooking the need to rotate or revoke keys over time. Key management policy must include lifecycle controls.
• Enterprise Usage: Popular for single sign-on. Relies on time-synchronized session tickets, so clock drift is a frequent source of failure.
• Security Considerations: If the KDC (Key Distribution Center) is compromised, the entire realm’s security collapses.
• Operational Complexity: Cross-realm trust and multi-organization setups can be cumbersome.
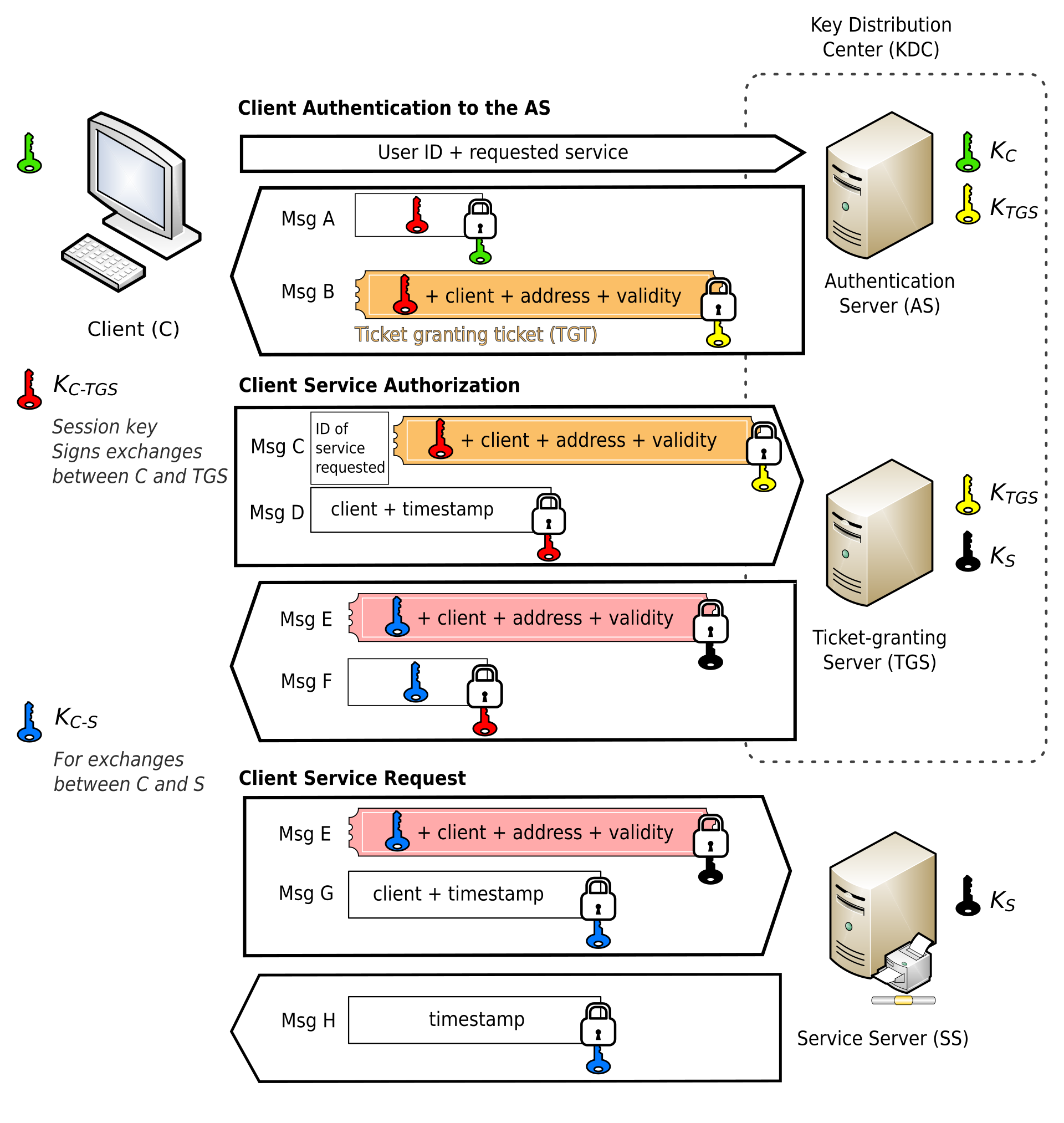
PKI (public-key certificates, roots of trust, TLS/SSL) RFC 5280 (PKI X.509)
• Revocation Challenges: CRLs and OCSP often not checked strictly; failure modes and stale revocation info remain unsolved pain points.
• Root Stores: Systems trust a set of roots, typically managed by OS/browser vendors (e.g., Mozilla, Microsoft). Relying parties seldom question them, even if some are compromised or out-of-date.
Key Storage & Infrastructure
• Trusted Execution Environments (TEEs)
• Cloud-based KMS (See Cosmian, Hashicorp)
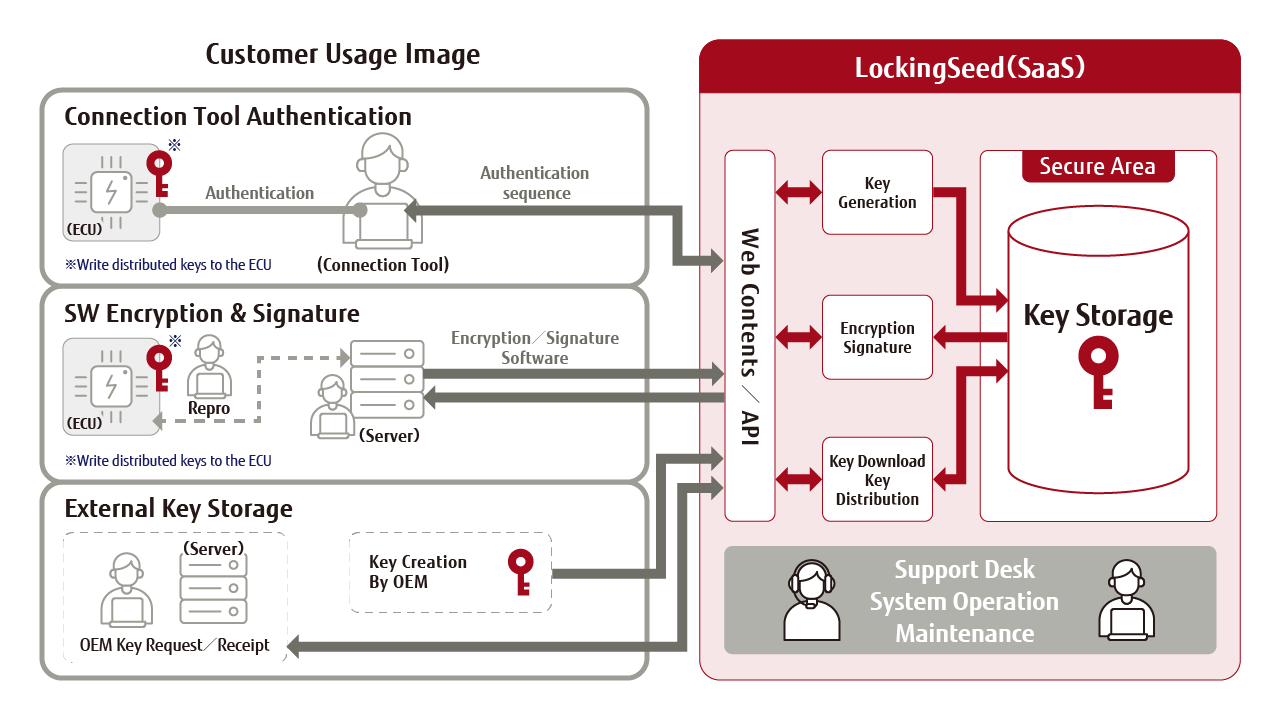
Granular Key Management
(Overhead grows with policy complexity; also demands efficient revocation of attributes or re-issuing cryptographic material.)
• Identity-based or attribute-based (keys tied to user identity, attributes) and access control logic embedded in the encryption process.
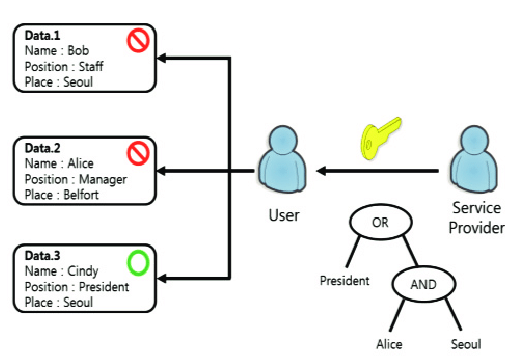
• Policy-based (keys granted or revoked based on organizational or contextual rules) relies on external policy engines to decide who gets keys in real time, typically using classical encryption methods.
Too Many Options: A Survey of ABE Libraries for Developers
Example of attribute-based policy with a real world implementation at Cosmian
2. Distributed & Decentralized Approaches
(Many of these methods are lacking standards or have emerging standards)
• Threshold / Secret Sharing → n-of-m reconstruction (Practical Threshold Signatures, Fast Multiparty Threshold ECDSA with Fast Trustless Setup)
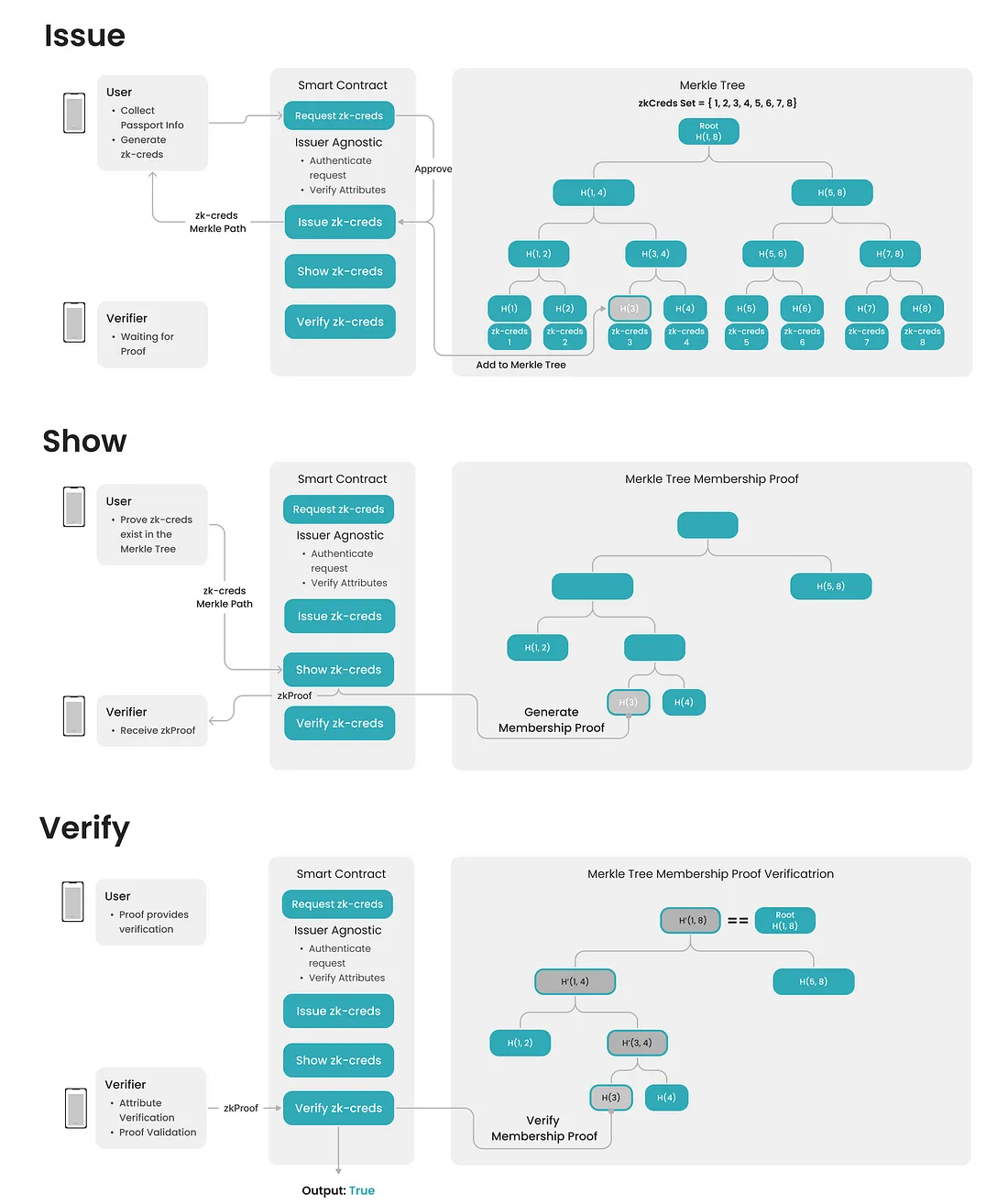
• DID + Blockchain → decentralized identifiers, peer-to-peer attestations (w3c DID Specification, zkCreds)
• Smart Contracts & Social Recovery → a blockchain-based approach to recover keys (Why we need wide adoption of social recovery wallets)
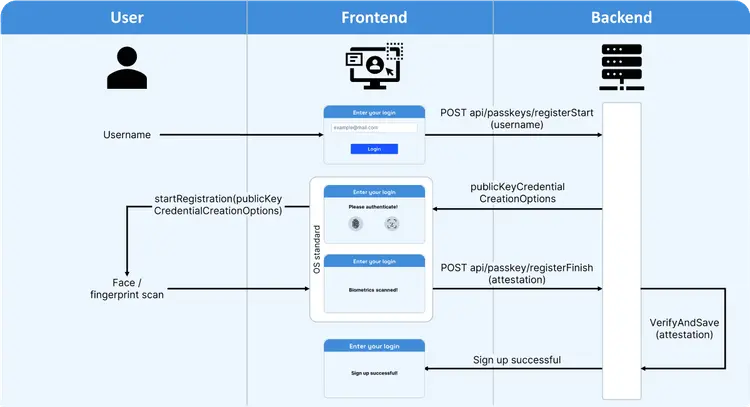
• Passkeys / Hardware Modules → storing private keys in physical devices (e.g., FIDO tokens) (FIDO2: WebAuthn)
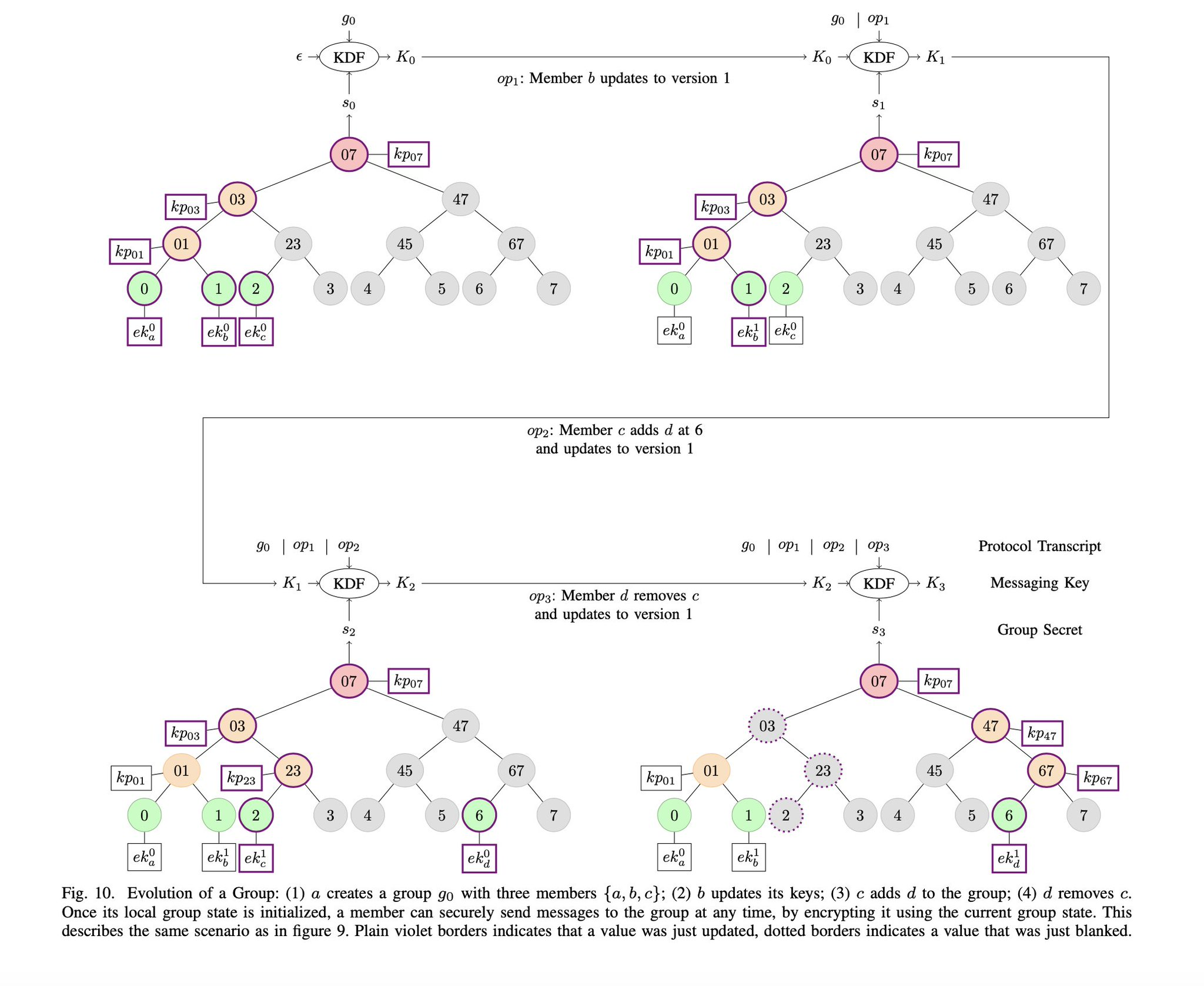
• Tree-Based Key Management → for large-scale group comms (video conferencing, secure messaging) (TreeKEM, Keyhive lab notebook)
Passkeys
zkCreds
3. Post-Quantum & Other Emerging Technologies
• Post-Quantum Cryptography (PQC) (Post-quantum cryptography — dealing with the fallout of physics success)
• Lattice-based (e.g., Kyber)
• Isogeny-based (SIDH-like constructions)
• Hybrid PQC + classical, or dedicated post-quantum KEM
• Zero-Knowledge Proofs (ZKPs) for privacy-preserving proofs (Noir, SP1)
• Proxy Re-Encryption (PRE) for reassigning ciphertext recipients without decryption
(Here I have not included methods using quantum cryptography.)
color mode